Vulnerability scanning
Introduktion
Scans networks and systems for known vulnerabilities
Over 50 new vulnerabilities are discovered every day. These are vulnerabilities that increase the risk of intrusion into your business. Our vulnerability scanning tool scans your system, server, firewall or website and reveals what vulnerabilities exist. It also tests whether everything is properly configured so that nothing that should be private, with easy access, is public.
Vulnerability scanning
Find and fix the vulnerabilities in your systems, servers and networks – before someone else does!
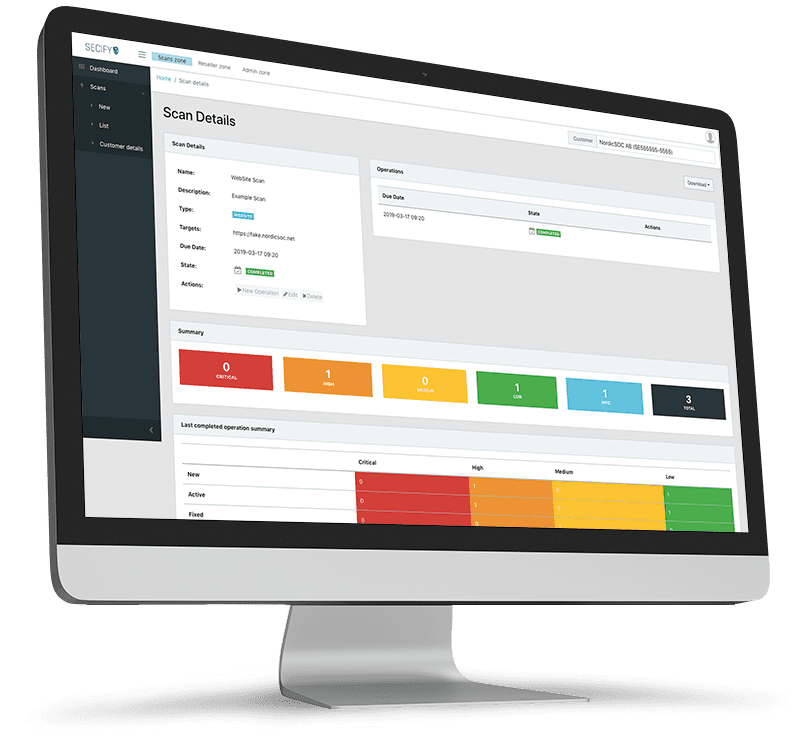
Conducting vulnerability scans and then addressing the vulnerabilities strengthens the organization’s protection against cyberattacks. Our tool identifies vulnerabilities and gives you an overview, but also a detailed picture of how vulnerable your different systems are and how to fix them.
After a completed vulnerability scan, you will receive two different reports. A summarized overview report that you can use to show your management the security challenges you face (executive), as well as an in-depth detailed report showing all vulnerabilities in detail.
We recommend ongoing vulnerability scans once a month on key systems. This allows you to plug holes and find potential misconfigurations and security gaps before they are exploited. This will also allow you to better monitor the progress of the action.
Några av våra kunder








Our packages
Three levels to choose from
Our vulnerability scan is divided into three different levels with different content in each package. For each package, there is also the possibility to add a number of add-ons. More on this can be found under the heading ‘Supplements’.
For all our packages, we recommend that you carry out an initial threat assessment. It will give you an overall picture of the threats facing your organization.
Want more?
Additional services to the packages
If you want more, there are a number of add-ons you can choose from*. The surcharges can be applied to all our packages. You can easily order by contacting one of our sales representatives.
- Excel version of the report
The report containing all vulnerabilities is sent as an Excel file - Verification of false positives
An additional manual check of the vulnerabilities - Inventory of networks
We receive a list of IP addresses that are all scanned - Review of the results with an IT security consultant
For one hour, we go through the results together and find a way forward
*For those who have needs that are not covered by the above, we are good at finding a solution.
Vulnerability scanning and
pentest is not the same thing
But in our range of services, they are very close at hand. A penetration test, or pentest, is an extended form of vulnerability scanning where the data (i.e. the results of the vulnerability scan) is used as a starting point to manually attempt to enter the system.
If the system is connected to the network or contains information assets that are important to the business, we recommend that you perform a pentest, as a next step to determine which vulnerabilities are most critical to fix. You can read more penetration tests on our services page.
Questions and answers
Find answers to the most frequently asked questions about vulnerability scanning. Do you have a question that is not listed? Use the contact form further down the page.





